
CyCraft MDR Tested Against MITRE Engenuity-Emulated Threat Group Simulations, Latest Round Includes WizardSpider and Sandworm
Taipei, Taiwan—31 March 2022—CyCraft Technology, a world-leading cybersecurity firm based in Taiwan, is proud to have participated in the fourth round of MITRE Engenuity ATT&CK Evaluations. This round of independent ATT&CK Evaluations for enterprise cybersecurity solutions emulated the infamous Wizard Spider and Sandworm threat groups.
This is CyCraft’s third time participating in the ATT&CK Evaluations. CyCraft first joined the second round of evaluations back in 2019, becoming the first cybersecurity vendor from Taiwan—and second from Asia—to participate. This latest round of evaluations saw the largest turnout of cybersecurity vendors to date.
MITRE, the ATT&CK framework, and Cybersecurity Vendor Evaluations
In 2018, the MITRE Corporation, a not-for-profit American organization that works in the public interest, launched the MITRE ATT&CK Evaluations, where MITRE evaluates the efficacy of cybersecurity products using an open methodology based on their own publicly available ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) Framework—a living, growing framework of common tactics, techniques, and procedures (TTP) used by advanced persistent threats (APTs) and other cybercriminals. Everything a hacker can do on a victim’s system can be uniquely represented in the ATT&CK Framework.
The ATT&CK Evaluations not only provide transparency and publicly available data on the true efficacy of cybersecurity products but also drive security vendors to enhance their defensive capabilities towards known adversarial behaviors. Each round of ATT&CK Evaluations has cybersecurity vendors pitting their solutions against MITRE team-created emulations of known APTs. Previous rounds include emulations of APT3 (China), APT29 (Russia), Carbanak & FIN7 (financially-motivated threat groups).
Round 4
For Round 4, MITRE Engenuity used the MITRE ATT&CK knowledge base to emulate the techniques, tactics, and procedures (TTP) of the infamous threat groups Wizard Spider and Sandworm. These two threat actors were chosen based on their complexity and relevancy to the market. Wizard Spider is a financially motivated Russia-based threat group that has been conducting ransomware campaigns since August 2018 against a variety of organizations, ranging from major corporations to hospitals. Sandworm is a destructive threat group known for carrying out notable attacks such as the 2015 and 2016 targeting of Ukrainian electrical companies and 2017’s NotPetya attacks. Sandworm has been attributed to Russia’s General Staff Main Intelligence Directorate (GRU) Main Center for Special Technologies (GTsST) military unit 74455.
“This latest round indicates significant product growth from our vendor participants. We are seeing greater emphasis in threat-informed defense capabilities, which in turn has developed the infosec community’s emphasis on prioritizing the ATT&CK Framework,” said Ashwin Radhakrishnan, acting General Manager of ATT&CK Evaluations at MITRE Engenuity.
The MITRE Engenuity ATT&CK Evaluations team chose to emulate two threat groups that abuse the Data Encrypted For Impact (T1486) technique. Wizard Spider has leveraged data encryption for ransomware, including the widely known Ryuk malware (S0446). Sandworm, on the other hand, has leveraged encryption for the destruction of data, perhaps most notably with their NotPetya malware (S0368) that disguised itself as ransomware. While the common thread to this year’s evaluations is “Data Encrypted for Impact,” both groups have substantial reporting on a broad range of post-exploitation tradecraft.
For full results from the ATT&CK Evaluations, please visit https://attackevals.mitre-engenuity.org/enterprise/wizard-spider-and-sandworm/.
Everything Starts From Security
CyCraft Technology autonomous security products have a proven track record of dealing with cyberattacks targeting critical infrastructure linked and/or affiliated with nation-states, including Russia and China. In 2021, CyCraft released a working decryptor for Prometheus ransomware who, at the peak of their activity, targeted multiple critical infrastructure organizations in over 30 different countries in only 4 months. In 2022, CyCraft unveiled a months-long smokescreen supply chain attack targeting Taiwan’s financial sector; evidence uncovered during an incident response investigation implicates ties these attacks to APT10—a China state-sponsored hacker group widely believed to be associated with the Chinese Intelligence Agency, the Ministry of State Security (MSS).
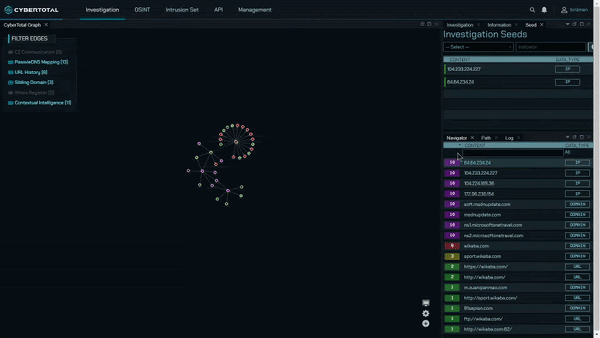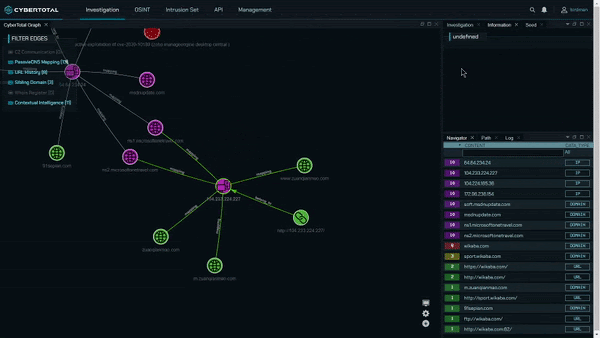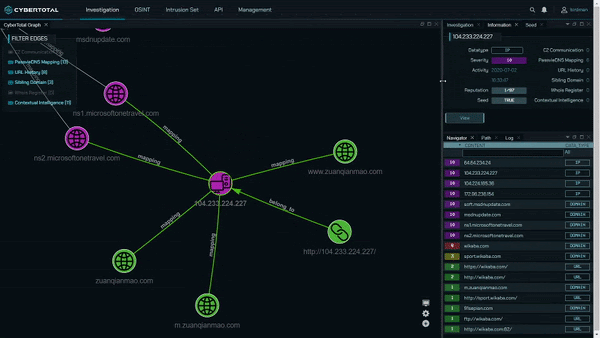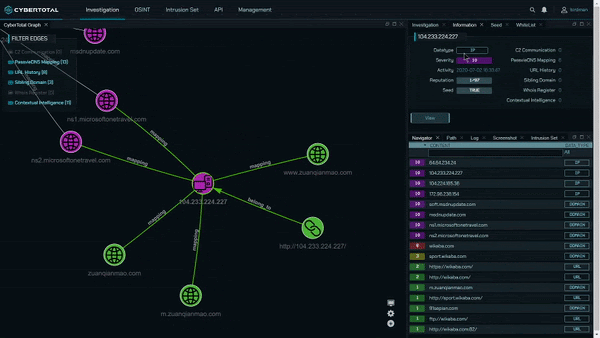
CyberTotal, the CyCraft AIR Cyber Threat Intelligence Platform
CyCraft Managed Detection and Response (MDR) cybersecurity services provide enterprises with continuous digital forensic investigation capabilities. CyCraft customers experiencing a cyberattack ascertain the ground truth to the attack via real-time cyber situation reports, providing a complete attack storyline, root cause analysis, alert triage automation, and malicious domain, IP, URL analysis.

CyCraft Leadership (right to left): Benson Wu, CEO; Jeremy Chiu, CTO; PK Tsung, CSO
“CyCraft MDR automates investigations and alert verifications, providing SOC teams with the ground truth to an attack faster and more hands-off than existing solutions. Our fast, accurate, simple, thorough AI-driven approach to cybersecurity has led CyCraft to manage millions of endpoints from both government and enterprise customers in over a dozen countries worldwide.”
—Benson Wu, CyCraft Founder & CEO
About MITRE Engenuity ATT&CK Evaluations
MITRE Engenuity ATT&CK Evaluations are paid for by vendors and are intended to help vendors and end-users better understand their products’ capabilities in relation to MITRE’s publicly accessible ATT&CK framework. MITRE developed and maintains the ATT&CK knowledge base, which is based on real-world reporting of adversary tactics and techniques. ATT&CK is freely available and is widely used by defenders in industry and government to find gaps in visibility, defensive tools, and processes as they evaluate and select options to improve their network defense. MITRE Engenuity makes the methodology and resulting data publicly available so other organizations may benefit and conduct their own analysis and interpretation. The evaluations do not provide rankings or endorsements.
About MITRE Engenuity
MITRE Engenuity, a subsidiary of MITRE, is a tech foundation for the public good. MITRE’s mission-driven teams are dedicated to solving problems for a safer world. Through our public-private partnerships and federally funded R&D centers, we work across government and in partnership with industry to tackle challenges to the safety, stability, and well-being of our nation.
MITRE Engenuity brings MITRE’s deep technical know-how and systems thinking to the private sector to solve complex challenges that government alone cannot solve. MITRE Engenuity catalyzes the collective R&D strength of the broader U.S. federal government, academia, and private sector to tackle national and global challenges, such as protecting critical infrastructure, creating a resilient semiconductor ecosystem, building a genomics center for public good, accelerating use case innovation in 5G, and democratizing threat-informed cyber defense.
About CyCraft
CyCraft secures government agencies, financial institutions, semiconductor manufacturing, police and defense organizations, Fortune Global 500 firms, airlines, telecommunications, SMEs, and more by being Fast / Accurate / Simple / Thorough.
CyCraft automates information security protection with built-in advanced managed detection and response (MDR), global cyber threat intelligence (CTI), smart threat intelligence gateways (TIG), network detection and response (NDR), security operations center (SOC) operations software, auto-generated incident response (IR) reports, enterprise-wide Health Check (Compromise Assessment, CA), and Secure From Home services. CyCraft also collaborates with other cybersecurity organizations, including the International Forum of Incident Response & Security Teams (FIRST) and the Taiwan Cybersecurity Center of Excellence (CCoE).
Meet your modern cyber defense needs by engaging CyCraft at engage@cycraft.com
Contacts
Dr. Benson Wu
Co-Founder & CEO, CyCraft Technology
benson.wu@cycraft.com
Chad Duffy
VP of Strategy, CyCraft Technology
chad.duffy@cycraft.com
Contact Information:
Name: Chad Duffy
Email: chad.duffy@cycraft.com
Job Title: VP of Strategy
Tags:
Menafn, IPS, Reportedtimes, Google News, Financial Content, ReleaseLive, PR-Wirein, CE, Extended Distribution, iCN Internal Distribution, English
Contact Information:
Name: Chad Duffy
Email: chad.duffy@cycraft.com
Job Title: VP of Strategy

